TECH PARTNERS
3 Reasons To Use Cyberstorage for Ransomware Mitigation
3 Reasons To Use Cyberstorage for Ransomware Mitigation
Cyberstorage technology is growing in popularity as organizations look for simple “one-and-done” ransomware mitigation.
The latest ransomware evolution exposes a gap
Ransomware attacks have evolved in recent years, and how attacks are monetized has changed significantly. A current trend in ransomware is double extortion– a ransomware attack in which a copy of data is first stolen or exfiltrated with the threat to publish online in retaliation for unpaid ransoms. Businesses now need to consider how to keep their company running with the shortest downtime after an attack, along with securing their data daily to avoid having it stolen. Since the first reported double extortion attack in 2020, double extortion has been seen in over 83% of recorded cases. This change in monetization strategy has helped ransomware damages skyrocket to tens of billions of dollars annually.
The success of double extortion ransomware attacks highlight a gap in traditional security stack. What happens when perimeter defenses, such as endpoint security or firewalls, fail to keep malware out? What if misconfiguration or backdoor vulnerability allows an attacker access to your stored cloud data or backup copies? Today’s businesses need creative solutions to tackle data theft and exfiltration head-on to detect and remediate intrusion as quickly as possible.
Cyberstorage emerges in response to data exfiltration
Emerging solutions fuse high-performance cybersecurity technology with accessible storage to maintain day-to-day operations. The term for this data-first security approach is cyberstorage. Introduced as a new category in Gartner’s Hype Cycle for 2022 Innovation Trigger section, Gartner defines cyberstorage as a solution that “protects storage system data against ransomware attacks through early detection and blocking of attacks, and aids in recovery through analytics to pinpoint when an attack started.” Essentially, cyberstorage is the broad term for a layer of technology that sits between the system infrastructure and the data storage systems and focuses on protecting the data itself instead of the network perimeter or storage media that holds it.
Three reasons to implement cyberstorage today
- Cyberstorage blocks attacks to storage system data automatically
A cyberstorage solution includes built-in, proactive technology that can recognize anomalies within the data vault, such as errant processes or unauthorized access and removal of files. Cyberstorage technology will jump into action on its own by automatically quarantining the threat location and alerting and logging the activity for further investigation.
- Cyberstorage uses intelligence to take action and remediate
After quarantining the threat location, a cyberstorage solution then self-heals the compromised data automatically, ensuring the organization can still access a clean copy of stored data and eliminating costly downtime.
- Cyberstorage prevents data from being copied offsite in a readable format, even if a backdoor vulnerability was used
Cyberstorage is purpose-built to withstand data exfiltration attacks. If a hacker were to breach a cloud storage bucket, multiple safeguards at the data level ensure that the data will remain meaningless and unusable to them. Companies can maintain the upper hand in responding to ransom demands knowing that bad actors only hold scrambled, unusable data.
Immutable data and cyberstorage work great together.
Data backups were originally intended as a failover in the event of an outage caused by a natural disaster, but are now a critical component of a ransomware response strategy. Object-level immutability has become an important measure for protecting data in the event of an attack. Immutability ensures that data cannot be altered in any way during the set retention period, including being deleted or maliciously encrypted by ransomware. Used together, these data-first security technologies ensure data integrity throughout the lifecycle of an attack. Immutability protects files inside the data vault, while cyberstorage adds critical hands-off security: automatic detection, response, and the means to ensure that even copied or stolen data remains unusable to threat actors. Together, they create a nearly impenetrable cloud storage vault that offers granular configurations and in-depth insights into an attack.
Start evaluating cyberstorage for your environment
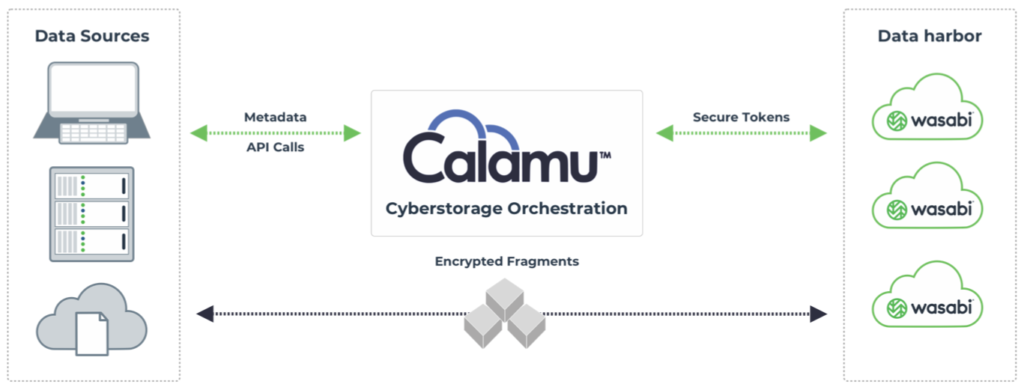
Cyberstorage is intended to work with environments such as Wasabi hot cloud storage and can add a valuable layer of security and resilience. Seamless integration simplifies the path to secure hybrid or multi-cloud storage and ensures easy deployment for IT administrators. Calamu and Wasabi have partnered together to offer affordable cyberstorage vaults. Ready to learn more? Read the Calamu and Wasabi solution overview.
the bucket
The latest ransomware evolution exposes a gap
Ransomware attacks have evolved in recent years, and how attacks are monetized has changed significantly. A current trend in ransomware is double extortion– a ransomware attack in which a copy of data is first stolen or exfiltrated with the threat to publish online in retaliation for unpaid ransoms. Businesses now need to consider how to keep their company running with the shortest downtime after an attack, along with securing their data daily to avoid having it stolen. Since the first reported double extortion attack in 2020, double extortion has been seen in over 83% of recorded cases. This change in monetization strategy has helped ransomware damages skyrocket to tens of billions of dollars annually.
The success of double extortion ransomware attacks highlight a gap in traditional security stack. What happens when perimeter defenses, such as endpoint security or firewalls, fail to keep malware out? What if misconfiguration or backdoor vulnerability allows an attacker access to your stored cloud data or backup copies? Today’s businesses need creative solutions to tackle data theft and exfiltration head-on to detect and remediate intrusion as quickly as possible.
Cyberstorage emerges in response to data exfiltration
Emerging solutions fuse high-performance cybersecurity technology with accessible storage to maintain day-to-day operations. The term for this data-first security approach is cyberstorage. Introduced as a new category in Gartner’s Hype Cycle for 2022 Innovation Trigger section, Gartner defines cyberstorage as a solution that “protects storage system data against ransomware attacks through early detection and blocking of attacks, and aids in recovery through analytics to pinpoint when an attack started.” Essentially, cyberstorage is the broad term for a layer of technology that sits between the system infrastructure and the data storage systems and focuses on protecting the data itself instead of the network perimeter or storage media that holds it.
Three reasons to implement cyberstorage today
- Cyberstorage blocks attacks to storage system data automatically
A cyberstorage solution includes built-in, proactive technology that can recognize anomalies within the data vault, such as errant processes or unauthorized access and removal of files. Cyberstorage technology will jump into action on its own by automatically quarantining the threat location and alerting and logging the activity for further investigation. - Cyberstorage uses intelligence to take action and remediate
After quarantining the threat location, a cyberstorage solution then self-heals the compromised data automatically, ensuring the organization can still access a clean copy of stored data and eliminating costly downtime. - Cyberstorage prevents data from being copied offsite in a readable format, even if a backdoor vulnerability was used
Cyberstorage is purpose-built to withstand data exfiltration attacks. If a hacker were to breach a cloud storage bucket, multiple safeguards at the data level ensure that the data will remain meaningless and unusable to them. Companies can maintain the upper hand in responding to ransom demands knowing that bad actors only hold scrambled, unusable data.
Immutable data and cyberstorage work great together.
Data backups were originally intended as a failover in the event of an outage caused by a natural disaster, but are now a critical component of a ransomware response strategy. Object-level immutability has become an important measure for protecting data in the event of an attack. Immutability ensures that data cannot be altered in any way during the set retention period, including being deleted or maliciously encrypted by ransomware. Used together, these data-first security technologies ensure data integrity throughout the lifecycle of an attack. Immutability protects files inside the data vault, while cyberstorage adds critical hands-off security: automatic detection, response, and the means to ensure that even copied or stolen data remains unusable to threat actors. Together, they create a nearly impenetrable cloud storage vault that offers granular configurations and in-depth insights into an attack.
Start evaluating cyberstorage for your environment

Cyberstorage is intended to work with environments such as Wasabi hot cloud storage and can add a valuable layer of security and resilience. Seamless integration simplifies the path to secure hybrid or multi-cloud storage and ensures easy deployment for IT administrators. Calamu and Wasabi have partnered together to offer affordable cyberstorage vaults. Ready to learn more? Read the Calamu and Wasabi solution overview.
featured articles
WASABI MEDIA & ENTERTAINMENT
April 10, 2024
Introducing Wasabi AiR: Unleash the Power of AI wit...
Introducing Wasabi AiR: Unleash the Power of AI wi...
TECHNOLOGY
April 23, 2024
Responsible AI Use: Lessons from an Industry Inside...
Responsible AI Use: Lessons from an Industry Insid...
TECH PARTNERS HEALTHCARE
April 18, 2024
Protect Your Research Data with Cost-friendly, Powe...
Protect Your Research Data with Cost-friendly, Pow...
TECH PARTNERS
April 11, 2024
Addressing AI Infrastructure Challenges with Wasabi...
Addressing AI Infrastructure Challenges with Wasab...
VIDEO SURVEILLANCE
April 9, 2024





